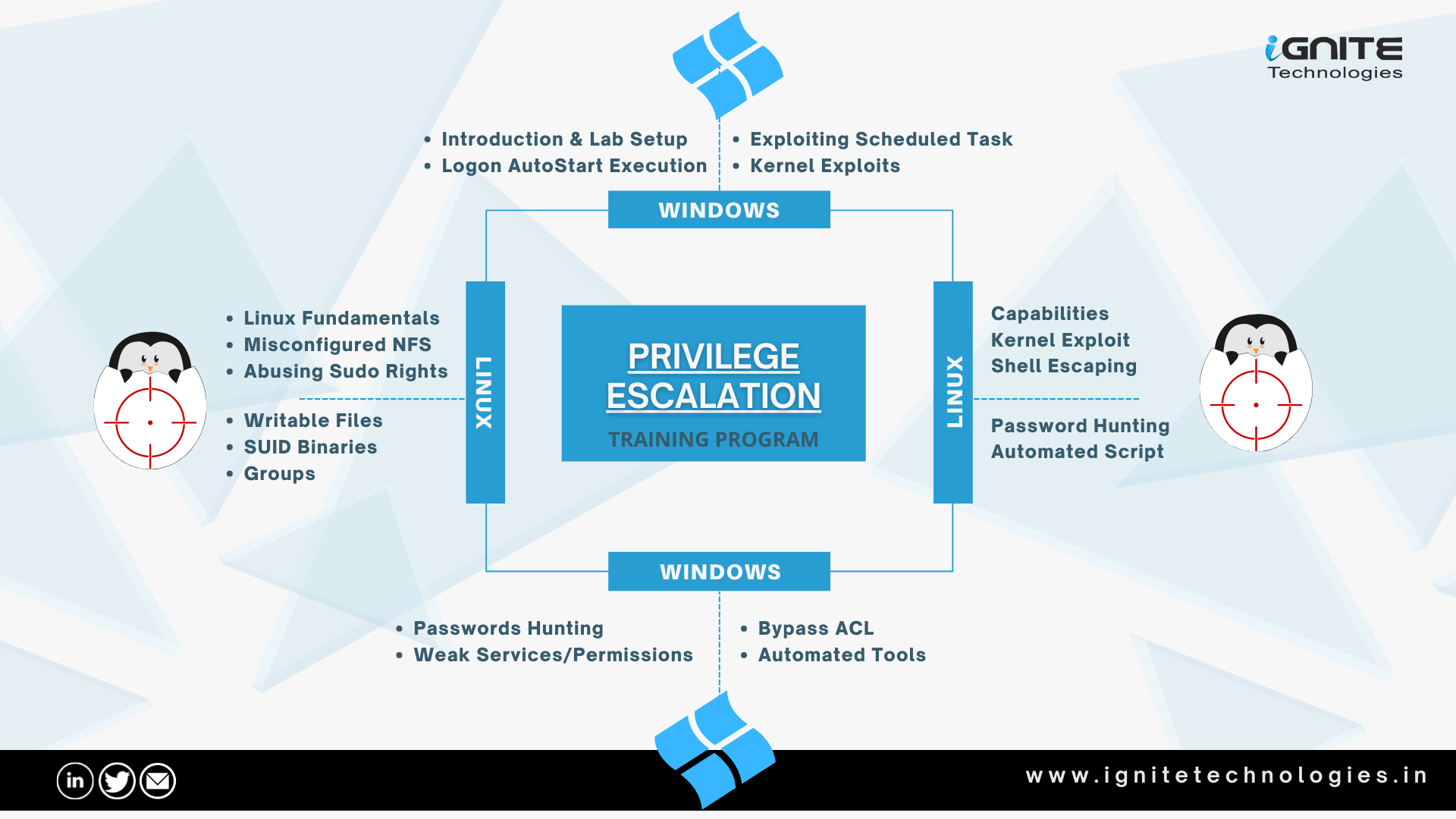
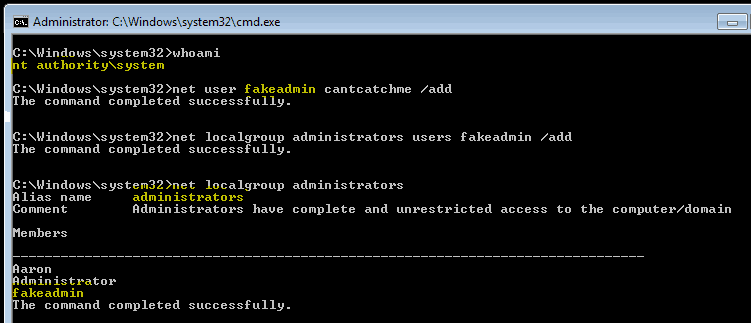
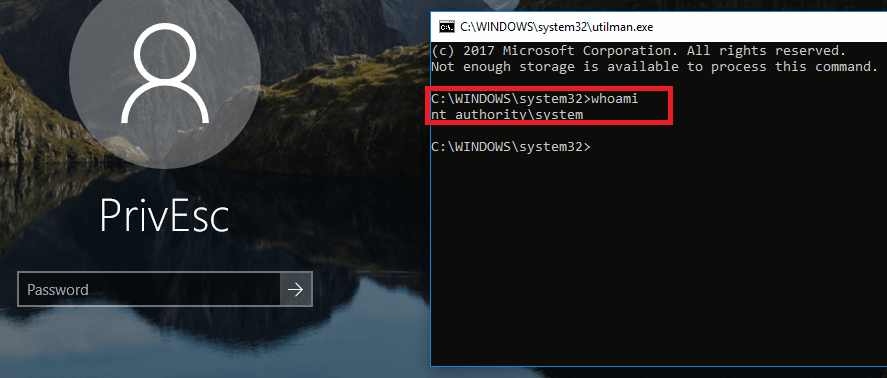
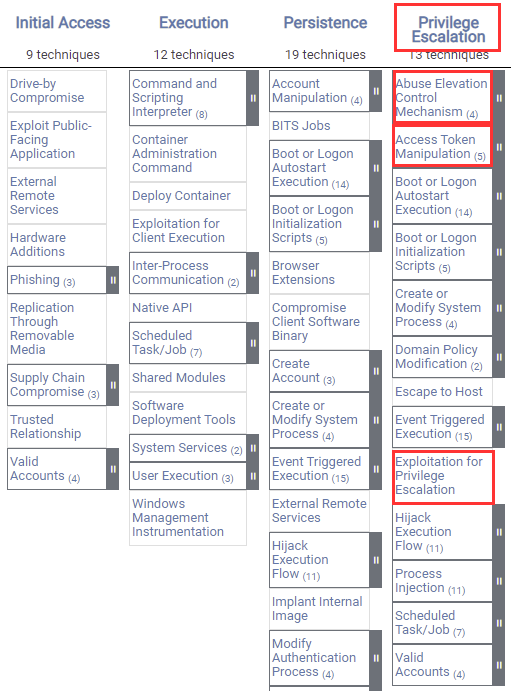
What Is A Privilege Escalation Attack? How To Prevent Privilege Escalation Attacks? - The Sec Master
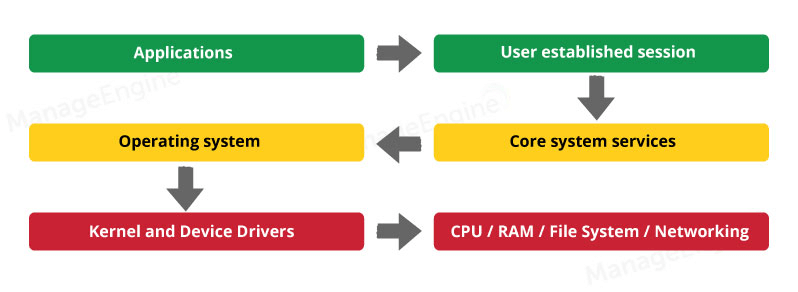
Privilege escalation | What you need to know and how to defend your network - ManageEngine Vulnerability Manager Plus

Linux Exploit Suggester - Linux Privilege Escalation Auditing Tool - Kali Linux 2018.1 – PentestTools

NoFilter: Tool that Escalates Privilege Abusing Windows Filtering Platform - GBHackers on Security | #1 Globally Trusted Cyber Security News Platform