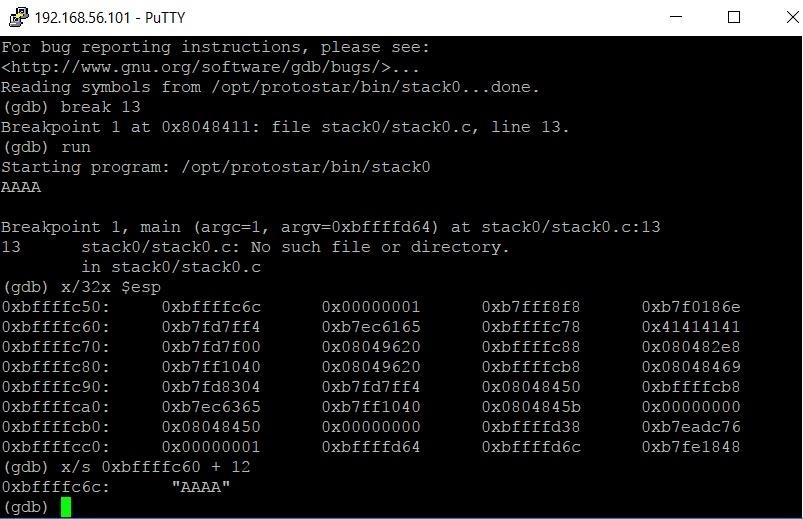
Unveiling the Power of Binary Exploitation: Mastering Stack-Based Overflow Techniques | by 0 day exploit | Medium

Cyber Detective💙💛 on X: "Offensive Security Checklists API testing Binary Exploitation testing Firewall testing Insecure deserialization Web and OT pentest and more. https://t.co/0FxzDoGET2 #pentest #cybersecurity https://t.co/3SzVLkClRW" / X















![Fall 23] Lec02: x86_64 / Shellcode / Tools - YouTube Fall 23] Lec02: x86_64 / Shellcode / Tools - YouTube](https://i.ytimg.com/vi/TfHFJa4OMwI/maxresdefault.jpg)