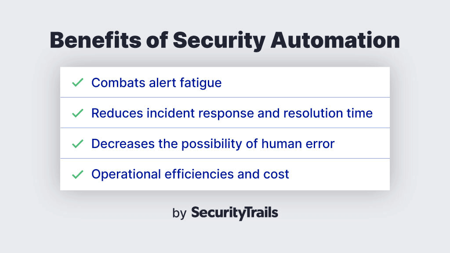
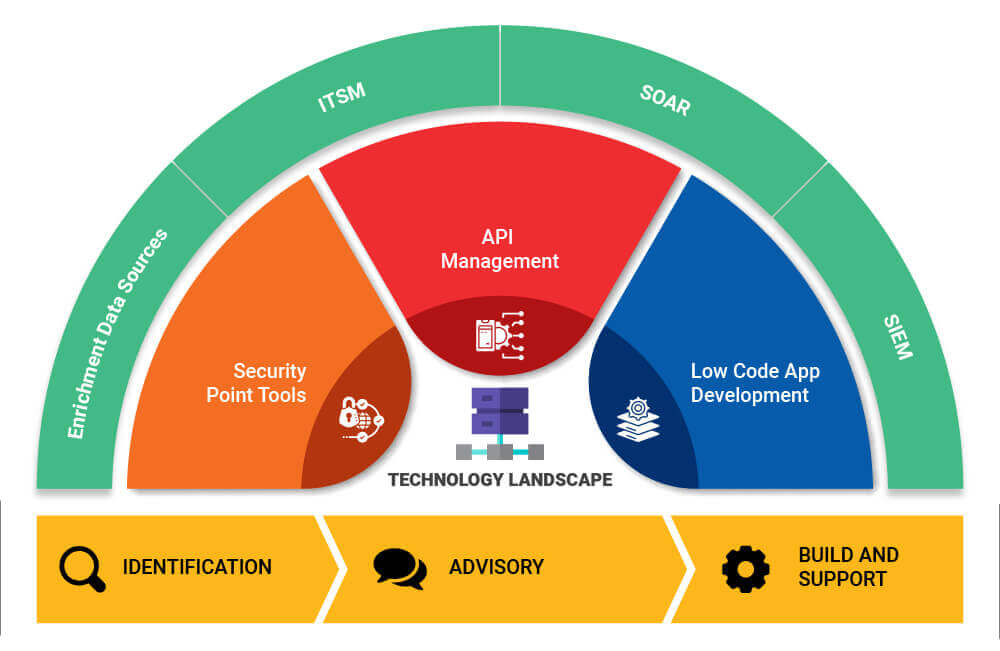
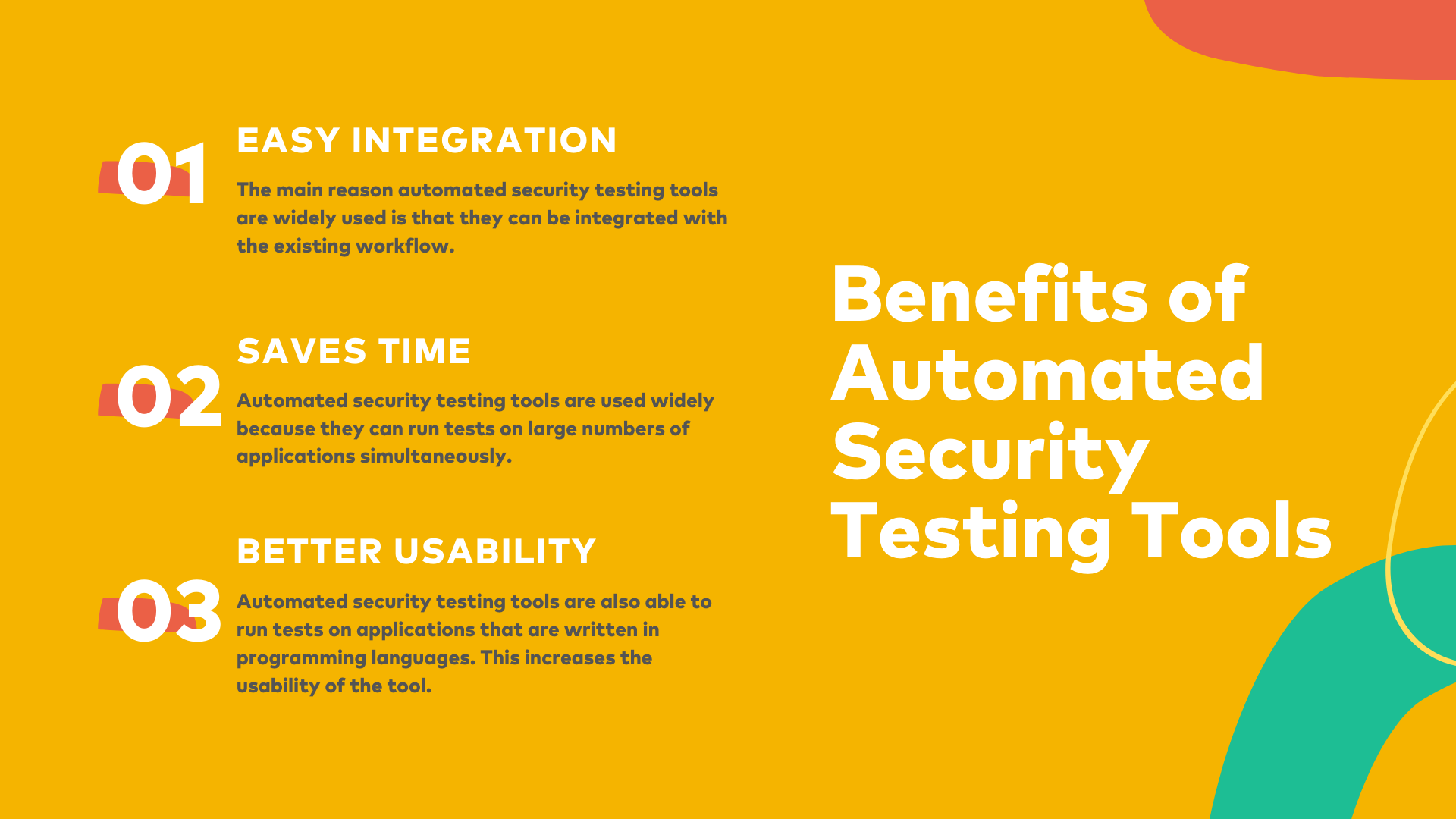
IT Security Automation Tools Integration Security Automation Integrates Tools Systems Summary PDF - PowerPoint Templates
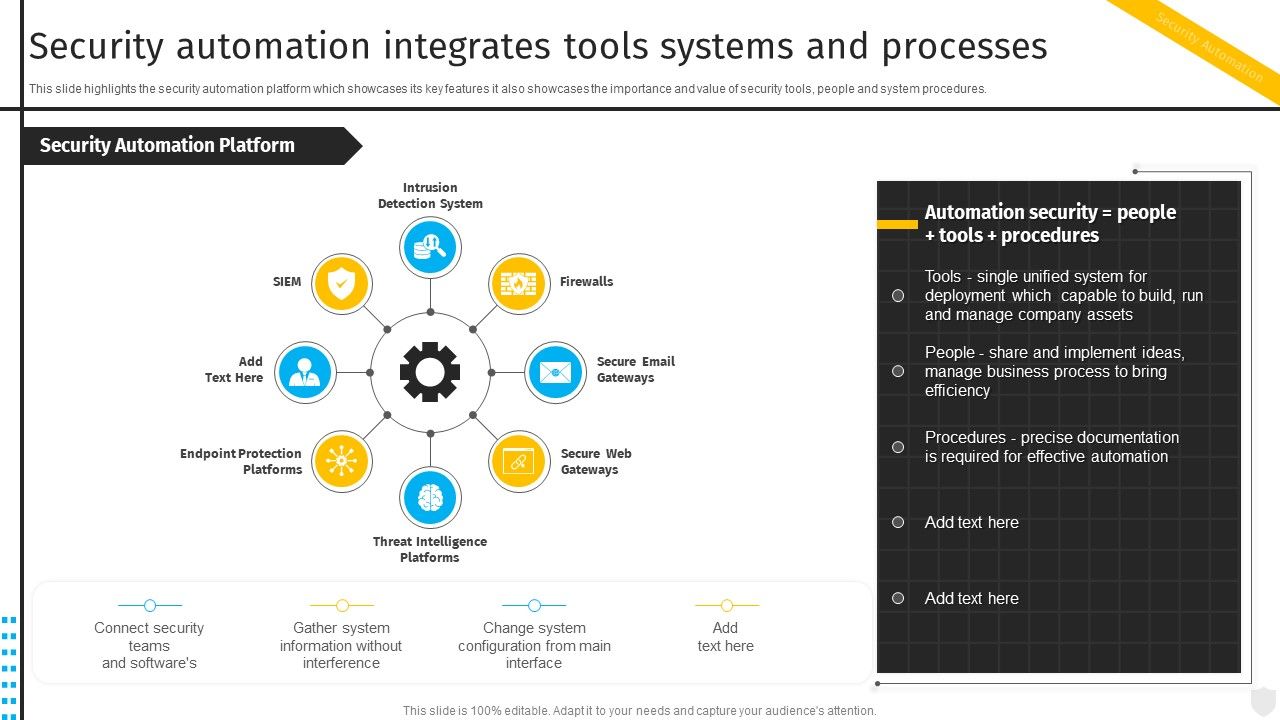
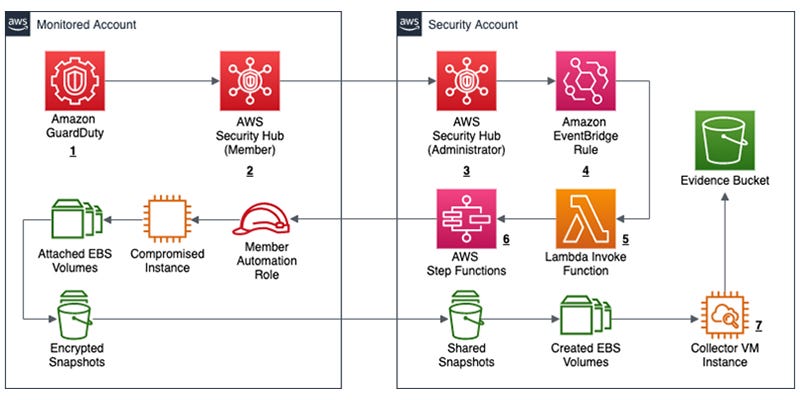
Security Automation Integrates Tools Systems And Security Automation To Investigate And Remediate Cyberthreats
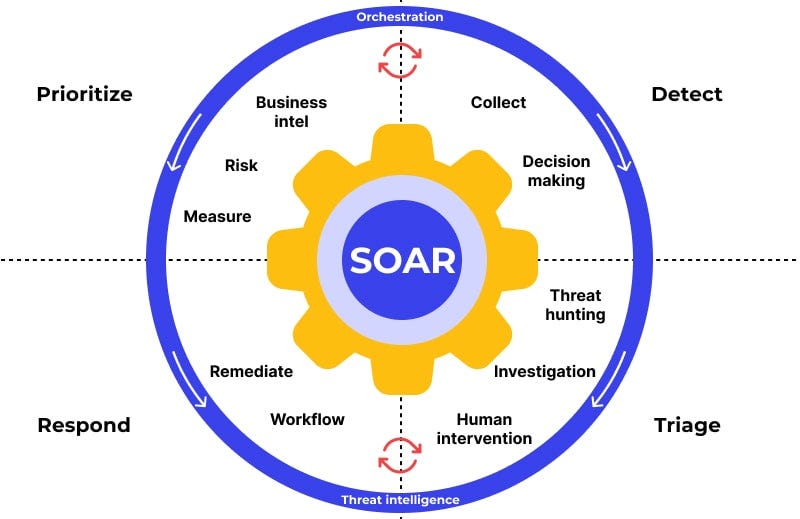
SOAR (Security Orchestration Automation and Response) Definition, Best Practices and Tools | by 0xffccdd | Medium